Tried a New Method for Implementing YubiOn FIDO Logon
- Shiraishi
- Nov 6, 2024
- 5 min read
Today, we released a new version (3.1.0.1) of YubiOn FIDO Logon.
In previous versions, registering a FIDO authenticator had to be done via the configuration tool or the management web interface. However, with this release, a new method has been added that allows users to register their FIDO authenticator during logon. While this may seem like a minor update compared to a major release, it is actually a handy feature when deploying FIDO Logon across an organization. We plan to introduce it in more detail on our blog as well.

Until now, when deploying FIDO Logon in an organization, software installation and initial setup could be handled collectively using AD or MDM features (Reference 1、Reference 2). However, when it came to registering the actual authenticators (security keys or smartphones), only the following methods were available:
① Distribute authenticators and have users register them using the setup tool
With this method, a common issue arises: users may not complete the registration of their authenticators. During this deployment flow, a policy allowing password logon is used until the authenticator is registered. If users do not register their authenticators, they will continue to log in with passwords indefinitely. Administrators must identify unregistered users via the management web and enforce registration through internal communication.
② Administrators pre-register authenticators via the management web and distribute them to users
This method avoids the issue of users failing to register their authenticators. However, the more users there are, the greater the burden on administrators. Also, in FIDO authentication, the PIN is supposed to be a knowledge factor known only to the user. But during registration, the administrator must know the PIN, which is not ideal. Depending on the operational method, sharing knowledge factors like passwords or PINs among multiple people is generally discouraged.
To address these issues, the latest update introduces a mechanism that forces users to register their authenticators during logon—they cannot log in without completing registration.Additionally, users can now set their own PINs during this registration process.
This enables a more secure and streamlined deployment process, as follows:
Set policy to enforce authenticator registration for accounts without one.
Pre-install FIDO Logon on user PCs and configure registration codes (via provisioning, AD, or MDM).
Distribute security keys to users (no need to pre-set PINs).
With these steps in place, users will be required to register their authenticators before logging in. This ensures that every account is protected by an authenticator, and users can set their own PINs, allowing for safer and more autonomous FIDO Logon operation.
■ Trying the New Deployment Method
Now, let’s try out the newly added deployment method and walk through the process of a user starting to use their PC. We’ll begin from the point where YubiOn FIDO Logon is already registered, the client app is installed on the PC, and the registration code is configured.

Before proceeding, we configure the necessary policy settings to enable this new deployment method.
We modify the default policy from its initial state as follows:
Restrict Sign-in Options | Enabled |
Logon for Accounts Without Registered Authenticators | Allow password logon only on the first attempt, then enforce authenticator registration |
With this setup complete, we’re ready to proceed.
From here, we’ll simulate the experience of a user logging into their account for the first time.
We assume a scenario where a local account named “YubiOn” has been created on the PC during provisioning, but the user has not yet logged in with that account(*1).
Each user has been provided with a brand-new YubiKey 5 NFC that has not been configured.
(*1) While this example uses a local account, the new feature also works with Microsoft accounts, AD accounts, and EntraID accounts.
① Perform Password Authentication
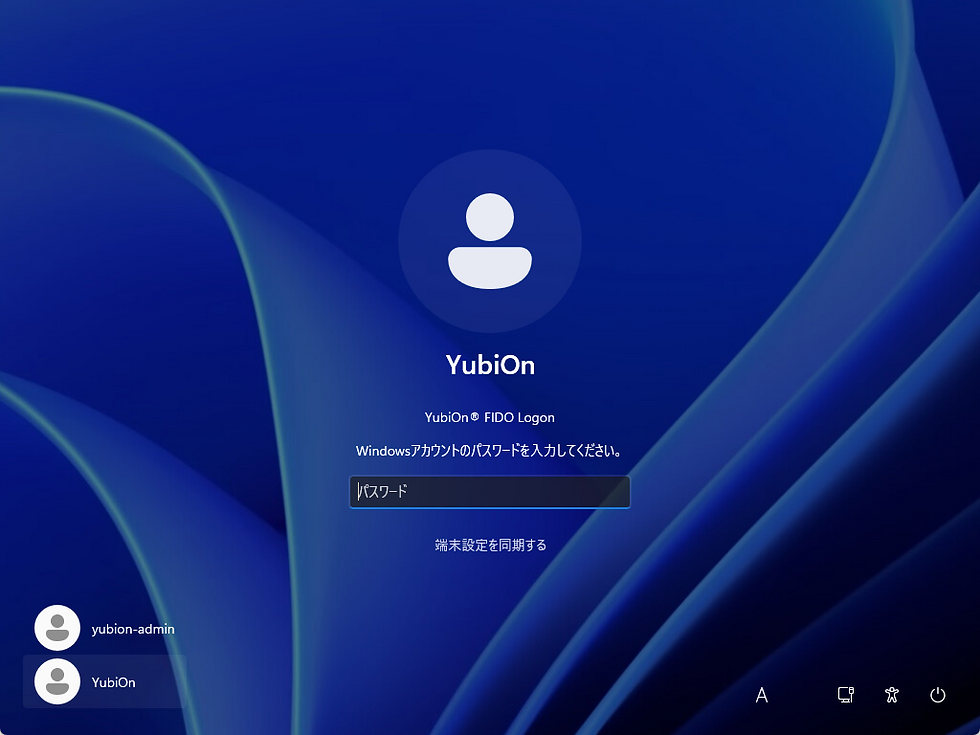
This is the logon screen of a PC where FIDO Logon has been installed and the registration code configured, but no authenticator has been registered yet.
Since the “YubiOn” account does not have an authenticator registered, the password input screen is displayed.

In previous versions, if password logon was allowed, users could log in simply by entering the correct password.
However, with the new enforcement of authenticator registration, users can no longer log in unless they register an authenticator at this stage.
② Set a PIN for the Security Key (if not already set)

As you proceed, you’ll be prompted to insert the authenticator into the USB port.
Follow the on-screen instructions and insert the security key.

Since the security key being used this time was in its original state with no PIN set, the system prompted for PIN setup.
Following the on-screen instructions, the user sets a PIN of their choice.

Since the PIN setup has been completed, we now proceed to register the authenticator
③ Register the Authenticator

To register the authenticator, you need to enter the PIN, so at this point, enter the PIN you just set.

You’ll be prompted to touch the security key to proceed with registration, so follow the instructions and touch the key to continue.

Now that the authenticator registration is complete, follow the on-screen instructions to proceed with authentication again.
④ Perform Authenticator for Logon
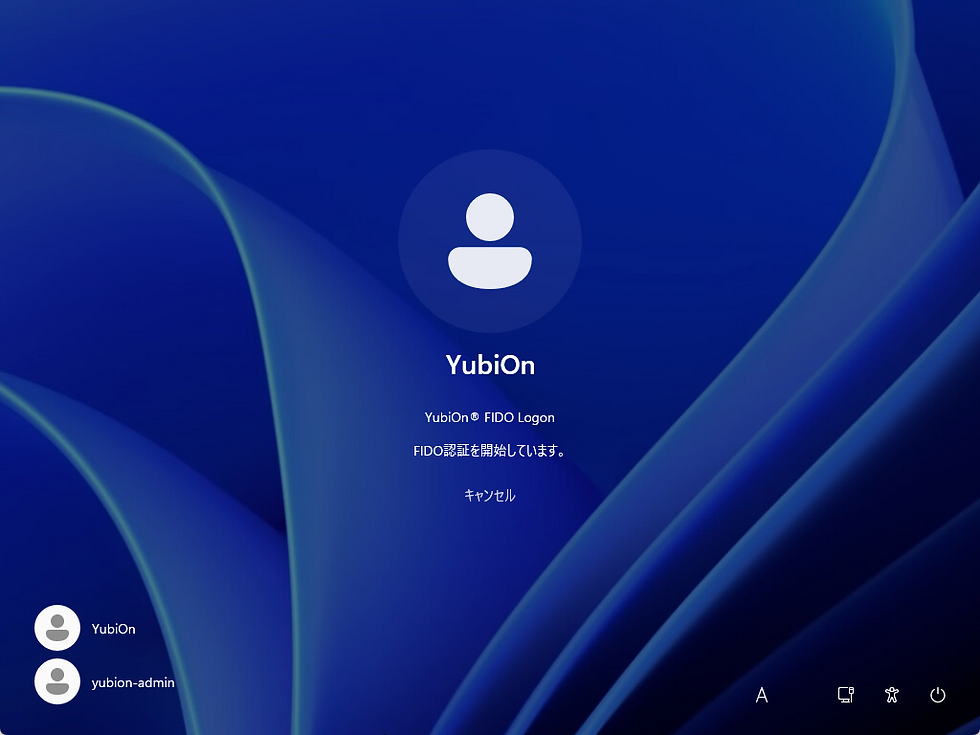 |  |  |
Since the registration and authentication flows in FIDO are almost identical on the surface, you proceed just as before, enter the PIN you set earlier, then touch the security key to complete authentication.
 |  |
When logging into Windows for the first time, the familiar welcome screen appears, and the account login is completed. These registration steps are only required once—after the authenticator is registered, users can log in and unlock the screen using the registered key from then on.
Previously, when using an authenticator registered via the setup tool for the first login, users also had to enter their account password. However, with this new flow, since the account password is entered at the beginning, there’s no need to enter it again when logging in with the FIDO authenticator immediately after registration.
■ Various Use Cases
In this example, we demonstrated using a security key with a local account, but this new feature also works with smartphone-based logon or remote Desktop logon. So it can be applied flexibly across different environments.
 |  |
When Registering a Smartphone

When Registering an Authenticator via Remote Desktop
■ Summary
Until now, deploying FIDO Logon at scale has posed operational challenges. Whether asking users to register their authenticators via the setup tool or having administrators pre-register them, there was always a need to manage and cover for registration gaps operationally.
With this update, users can now be required to register their authenticators, helping ensure safer PC usage and management. We hope this improvement will be a valuable aid in secure system administration.
A free version is available with the same features as the paid version for a three-month trial, so we encourage you to give it a try.
■ Related Links
[YubiOn FIDO Logon]
[YubiOn FIDO Logon Overview Page]




